Caged Spelunking
17 Jun 2019You can learn a lot by exploring an application’s ipa. Details like how it’s built, how it tracks its users and whether it has any obvious security vulnerabilities. This is all good information to know if you are looking to take a new job where they have existing apps. In this post I’m going to show how you can get some insights into existing apps without having to venture into jailbreaking.
Getting an ipa from the App Store
This is annoyingly fiddly but can be done like this:
- Download the app you want to investigate onto your device.
- Install
Apple Configurator 2from the app store and launch it. - Sign into your Apple account in
Apple Configurator 2. - Connect a device.
- Right click on your device and select
Add > Apps.... - Select the app you want to investigate and click
Add. - After some time you should be presented with an error dialog along the lines of:
The app named "Some App" already exists on "Your iPhone". - Use terminal (or navigate manually) to find the downloaded file in the following directory:
open ~/Library/Group\ Containers/K36BKF7T3D.group.com.apple.configurator/Library/Caches/Assets/TemporaryItems/MobileApps - Locate the
ipafor the app you are interested in and copy it somewhere else.
NB: You must copy before accepting the error dialog or theipawill be deleted.
Preparation
Now you have the ipa you can start to explore. Start by renaming the .ipa suffix to .zip and then double click the file to unzip.
Inside the zip you should find a file with a .app suffix, go ahead and remove the suffix to make exploration a little simpler.
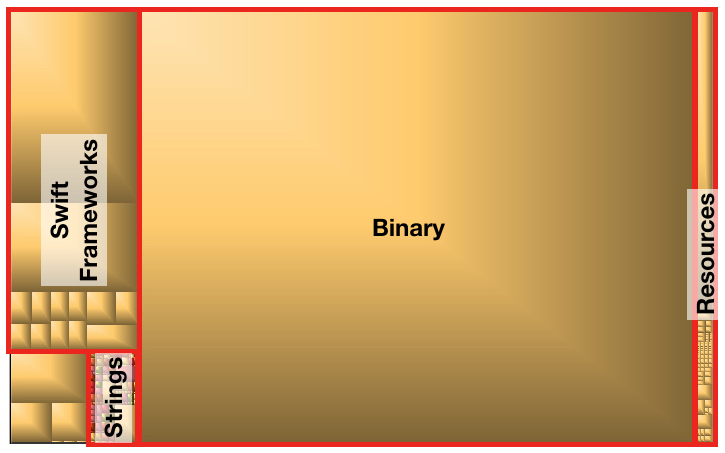
To help visualise the structure of an app I recommend using a tool like Grand Perspective, which will generate an interactive map of the used disk space.
Here’s what the diagram looks like for VLC for iOS:
Investigation
Now it’s just a case of poking around and seeing what is there. If you are exploring in preparation for an interview, then you should really be taking note of what you find and considering if you need to do any research into these things. Here’s some stuff that you might see and what it might mean:
*.car files
Indicates that this app uses Asset catalogues - these have been around for a while now but to brush up here’s the reference.
Frameworks directory
You can learn a lot about how an app is built by examining the contents of this folder. Questions to ask in here are:
- Are there too many dependencies?
- Are dependencies well maintained?
- The frameworks generally show their version information in their plist.
- This can be worrying especially if you can see a framework version being used that is known to be vulnerable.
- Are there creepy analytics SDKs?
- Is the app built using some Swift? The presence of libraries of the format
libSwift*indicates Swift is used.
Info.plist file
The Info.plist file contains all kinds of useful information:
It’s always worth looking in this file as it defines a lot of the app’s capabilities - here’s the reference. It’s also an easy place for developers to dump information (sometimes incorrectly) to use within the app, so there could be some secrets being exposed.
*.lproj directories
These folders are present in localised apps - the more folders there are the more territories that the app has been localised to.
If you want to read the contents of the *.strings files within these directories then go ahead and rename the extension from .strings to .plist.
*.momd directories
This directory shows that the app is using CoreData - here’s the reference.
To get a sense of what data is being stored you can peek in the *.mom files by renaming the the extension from .mom to .plist.
*.nib or *.storyboardc files
Not everyone is a fan of using interface builder so seeing a load of these in the ipa will either raise red flags or finally give you a reason to conquer that fear and give them another chance.
Settings.bundle directory
You can explore this by right clicking the file and selecting Show Package Contents.
Here’s the reference for settings bundles.
Dynamic Analysis
Doing the above is great for getting a look at how the app might be built but it’s also worth looking at how the app runs.
This is where I would be loading up Charles Proxy on my device and running the app to see what network requests are being made.
Once you have some network data you can ask questions like:
- Are they using
https? - Do the API requests being made look reasonable?
- Is the app quite chatty on the network?
- Are there any security issues or data being leaked within the requests?
Conclusion
You don’t have to go straight to jailbreaking devices to get a rough idea of how an app is built. I personally find this exploration interesting and really helpful when looking at potential career moves e.g. doing a bit of due diligence to make sure I’m not stepping into a burning app.